- Home
- TrainingEdit Content
-
Cyber Security
-
Project Management
-
Cloud
-
Networking
-
Compliance
-
Scrum & Agile
-
SAP
-
Customize
-
Business Tools
-
ITSM
Edit ContentEdit Content- Application Security Engineer (CASE) .NET
- CASE JAVA: Application Security Engineer JAVA (312-96)
- CCSE – Cloud Security Engineer (312-40)
- CEH – Ethical Hacker (CEH v11/ v12) / PT
- CHFI Computer Hacking Forensic Investigator-DFIR (312-49)
- Chief Information Security Officer (C|CISO 712-50)
- CPENT- Penetration Testing Professional (412-80)
- CSCU – Secure Computer User Certification (112-12)
- CTIA – Threat Intelligence Analyst (312-85)
- EC-Council Security Specialist (ECSS)
- EC-Council Disaster Recovery Professional (EDRP 312-76)
- ECES Certification: EC-Council Encryption Specialist (212-81)
- ECIH Certification | EC-Council Incident Handler (212-89)
- ECSA Certification | EC-Council Security Analyst (412-79)
- ECSA: EC-Council Security Analyst (Practical)
- Certified Ethical Hacker Practical (CEH v12)
- Network Defender CND (312-38) Certification
Edit ContentEdit Content- PMI Scheduling Professional (PMI-SP)
- PMI Risk Management Professional (PMI-RMP)
- Certified PMI Professional in Business Analysis (PMI-PBA)
- PMI Agile Certified Practitioner (PMI-ACP)
- Program Management Professional (PgMP) Certification
- Portfolio Management Professional (PfMP)
- Certified Associate Project Management (CAPM) Certification
- Certified Project Management Professional (PMP)
Edit ContentEdit Content- AWS : SAP on AWS – Specialty
- AWS Security Specialty (SCS-C02) Certification
- AWS Machine Learning – Specialty (MLS-C01)
- AWS Database Specialty (DBS-C01)
- AWS Data Analytics Specialty (DAS-C01)
- AWS Advanced Networking Specialty (ANS-C01)
- AWS SysOps Administrator – Associate (SOA-C02) | Cloud Admin
- AWS Developer Associate (DVA-C02)
- AWS Solutions Architect Associate (SAAC03)
- AWS DevOps Engineer Professional Certification (DOP-C02)
- AWS Solutions Architect Professional (SAP-C02) | Cloud Security
- AWS Cloud Practitioner (CLF-C02) | Cloud Computing
Edit ContentEdit Content- Google Professional Machine Learning Engineer
- Professional Google Workspace Administrator
- Google Professional Cloud Network Engineer
- Google Professional Cloud Security Engineer
- Google Professional Cloud DevOps Engineer
- Google Professional Data Engineer (GCP-PDE)
- Google Professional Cloud Developer
- Google Professional Cloud Database Engineer
- Google Professional Cloud Architect
- Google Associate Cloud Engineer
- Google Cloud Digital Leader (GCP-CDL)
Edit Content- Microsoft Identity and Access Administrator (SC-300)
- Microsoft Managing Modern Desktops (MD – 101)
- SC-900: Microsoft Security, Compliance, Identity Fundamentals
- Microsoft AZ-040T00: Automating Administration With PowerShell
- Microsoft Dynamics 365 Fundamentals (CRM): MB – 910
- Microsoft Windows Client (MD – 100)
- Microsoft Azure Data Fundamentals (DP – 900)
- Microsoft Azure Administrator (AZ – 104)
- Microsoft (AZ-400) Designing and Implementing Microsoft DevOps Solutions
- Microsoft – Data Engineering on Microsoft Azure (DP – 203)
- Microsoft Azure Security Technologies (AZ – 500)
- Microsoft Azure Fundamentals (AZ – 900)
Edit ContentEdit ContentEdit Content- Cisco DevNet Associate
- CCT Routing and Switching Certification
- CCT Data Center Certification
- CCT Collaboration Certification
- Cisco CyberOps Professional
- Cisco DevNet Professional
- Cisco CyberOps Associate Certification
- CCNA: Cisco Network Associate
- CCNP Data Center Certification
- CCNP Collaboration Certification
- CCNP Enterprise Certification
- CCDE Cisco Design Expert
- CCIE Enterprise Wireless Certification
- CCIE Enterprise Infrastructure Certification
- CCNP Service Provider Certification
- CCNP Security Certification
- CCIE Service Provider Certification
- CCIE Security Certification
- CCIE Data Center Certification
- CCIE Collaboration Certification
Edit ContentEdit ContentEdit ContentEdit Content- SAP Forecasting and Replenishment
- SAP on Google Cloud
- SAP Business Technology Platform (BTP) Event Mesh
- SAP CAR
- SAP PP
- SAP CBTA
- SAP Basis
- SAP Treasury Management
- SAP Marketing Cloud Key Features & Extensibility
- SAP Commerce cloud Business User Training ( Formerly HY200)
- SAP Complete module
- Sap Customer Data Cloud
- SAP Service Cloud
- SAP BI / BW
- SAP FI Vertex
- SAP Cloud applications studio
- SAP commerce cloud backoffice framework developer
- Sap Commisions (fka C4H430)
- SAP Commerce Cloud Developer Part – 2
- Sap Commerce Cloud Developer Part – 1
- SAP Solution Manager
- SAP information Lifecycle management
- SAP SD
Edit ContentEdit Content- Fortinet : NSE 7 – Enterprise Firewall Certification ( FT-EFW )
- Fortinet : NSE 6 – FortiSwitch Certification (FT-FSW)
- Securing AWS with FortiCloud Security
- Securing Azure with FortiCloud Security
- OT Security
- Fortinet : FortiSOAR Administrator (FT-FSR-ADM)
- Fortinet : FortiWeb Web Application Firewall (FT-FWB)
- Fortinet : FortiEDR – Endpoint Detection and Response
- Fortinet : FortiSIEM – Security Information & Event Management ( FT-FSM )
Edit ContentEdit Content -
- Enterprise Solution
- Resources
- Webinars
- LMS
- About us
- Contact us
- Home
- TrainingEdit Content
Cyber Security
Cloud Computing
Scrum and Agile
Business Tools
ITSM
Edit ContentSIEM & SOAR
- Qualys
- Splunk
- IBM Qradar
- FortiSIEM
- Arcsight
- Azure Sentinel
- LogRhythm
- Rapid7
- Trellix
- Cortex XSOAR
Firewall & SASE
- Fireye
- Checkpoint
- Forcepoint
- Fortinet
- Palo Alto
- Zscalar
- Netskope
IAM & PAM
- CyberARK
- Forgerock
- Beyond Trust
- PingID
- Cisco
Helpdesk & Ticketing
- Servicenow
- Sailpoint
- Salesforce
- Zoho
- Hubspot
- Jira
System Admin Tools
- Solaris
- NagiOS
- jProfiler
- Open LDAP
- Powerstore Backup
- Backup Cohesity
- Microsoft Endpoint Configuration manager
- Prisma Cloud Config check
- IBM System Automation
EDR
- Microsoft
- Qualys
- Trellix
- Crowdstrike
- Acronis
- Trend Micro
- SentineOne
VA and VM
- Tenable
- Acunetix
- OWASP ZAP
- Burp Suite
- Holm Security
- Nikto
- Qualys
Automation
- UiPath
- Power BI
- Robocorp
- PowerAutomate
- HashiCorp
ERP
- SAP
- SAP HANA
- Primavera
Edit Content-
Cyber Security
-
Project Management
-
Cloud
-
Networking
-
Compliance
-
Scrum & Agile
-
SAP
-
Customize
-
Business Tools
-
ITSM
Edit ContentEdit Content- Application Security Engineer (CASE) .NET
- CASE JAVA: Application Security Engineer JAVA (312-96)
- CCSE – Cloud Security Engineer (312-40)
- CEH – Ethical Hacker (CEH v11/ v12) / PT
- CHFI Computer Hacking Forensic Investigator-DFIR (312-49)
- Chief Information Security Officer (C|CISO 712-50)
- CPENT- Penetration Testing Professional (412-80)
- CSCU – Secure Computer User Certification (112-12)
- CTIA – Threat Intelligence Analyst (312-85)
- EC-Council Security Specialist (ECSS)
- EC-Council Disaster Recovery Professional (EDRP 312-76)
- ECES Certification: EC-Council Encryption Specialist (212-81)
- ECIH Certification | EC-Council Incident Handler (212-89)
- ECSA Certification | EC-Council Security Analyst (412-79)
- ECSA: EC-Council Security Analyst (Practical)
- Certified Ethical Hacker Practical (CEH v12)
- Network Defender CND (312-38) Certification
Edit ContentEdit Content- PMI Scheduling Professional (PMI-SP)
- PMI Risk Management Professional (PMI-RMP)
- Certified PMI Professional in Business Analysis (PMI-PBA)
- PMI Agile Certified Practitioner (PMI-ACP)
- Program Management Professional (PgMP) Certification
- Portfolio Management Professional (PfMP)
- Certified Associate Project Management (CAPM) Certification
- Certified Project Management Professional (PMP)
Edit ContentEdit Content- AWS : SAP on AWS – Specialty
- AWS Security Specialty (SCS-C02) Certification
- AWS Machine Learning – Specialty (MLS-C01)
- AWS Database Specialty (DBS-C01)
- AWS Data Analytics Specialty (DAS-C01)
- AWS Advanced Networking Specialty (ANS-C01)
- AWS SysOps Administrator – Associate (SOA-C02) | Cloud Admin
- AWS Developer Associate (DVA-C02)
- AWS Solutions Architect Associate (SAAC03)
- AWS DevOps Engineer Professional Certification (DOP-C02)
- AWS Solutions Architect Professional (SAP-C02) | Cloud Security
- AWS Cloud Practitioner (CLF-C02) | Cloud Computing
Edit ContentEdit Content- Google Professional Machine Learning Engineer
- Professional Google Workspace Administrator
- Google Professional Cloud Network Engineer
- Google Professional Cloud Security Engineer
- Google Professional Cloud DevOps Engineer
- Google Professional Data Engineer (GCP-PDE)
- Google Professional Cloud Developer
- Google Professional Cloud Database Engineer
- Google Professional Cloud Architect
- Google Associate Cloud Engineer
- Google Cloud Digital Leader (GCP-CDL)
Edit Content- Microsoft Identity and Access Administrator (SC-300)
- Microsoft Managing Modern Desktops (MD – 101)
- SC-900: Microsoft Security, Compliance, Identity Fundamentals
- Microsoft AZ-040T00: Automating Administration With PowerShell
- Microsoft Dynamics 365 Fundamentals (CRM): MB – 910
- Microsoft Windows Client (MD – 100)
- Microsoft Azure Data Fundamentals (DP – 900)
- Microsoft Azure Administrator (AZ – 104)
- Microsoft (AZ-400) Designing and Implementing Microsoft DevOps Solutions
- Microsoft – Data Engineering on Microsoft Azure (DP – 203)
- Microsoft Azure Security Technologies (AZ – 500)
- Microsoft Azure Fundamentals (AZ – 900)
Edit ContentEdit ContentEdit Content- Cisco DevNet Associate
- CCT Routing and Switching Certification
- CCT Data Center Certification
- CCT Collaboration Certification
- Cisco CyberOps Professional
- Cisco DevNet Professional
- Cisco CyberOps Associate Certification
- CCNA: Cisco Network Associate
- CCNP Data Center Certification
- CCNP Collaboration Certification
- CCNP Enterprise Certification
- CCDE Cisco Design Expert
- CCIE Enterprise Wireless Certification
- CCIE Enterprise Infrastructure Certification
- CCNP Service Provider Certification
- CCNP Security Certification
- CCIE Service Provider Certification
- CCIE Security Certification
- CCIE Data Center Certification
- CCIE Collaboration Certification
Edit ContentEdit ContentEdit ContentEdit Content- SAP Forecasting and Replenishment
- SAP on Google Cloud
- SAP Business Technology Platform (BTP) Event Mesh
- SAP CAR
- SAP PP
- SAP CBTA
- SAP Basis
- SAP Treasury Management
- SAP Marketing Cloud Key Features & Extensibility
- SAP Commerce cloud Business User Training ( Formerly HY200)
- SAP Complete module
- Sap Customer Data Cloud
- SAP Service Cloud
- SAP BI / BW
- SAP FI Vertex
- SAP Cloud applications studio
- SAP commerce cloud backoffice framework developer
- Sap Commisions (fka C4H430)
- SAP Commerce Cloud Developer Part – 2
- Sap Commerce Cloud Developer Part – 1
- SAP Solution Manager
- SAP information Lifecycle management
- SAP SD
Edit ContentEdit Content- Fortinet : NSE 7 – Enterprise Firewall Certification ( FT-EFW )
- Fortinet : NSE 6 – FortiSwitch Certification (FT-FSW)
- Securing AWS with FortiCloud Security
- Securing Azure with FortiCloud Security
- OT Security
- Fortinet : FortiSOAR Administrator (FT-FSR-ADM)
- Fortinet : FortiWeb Web Application Firewall (FT-FWB)
- Fortinet : FortiEDR – Endpoint Detection and Response
- Fortinet : FortiSIEM – Security Information & Event Management ( FT-FSM )
Edit ContentEdit Content - Enterprise Solution
- Resources
- Webinars
- About us
- Contact us
Home
>
Cyber Security
>
EC-Council
>
Certified Ethical Hacking
Certified Ethical Hacking Course (CEH® v12)
Get ready to ace your CEH® v12 exam in the first go with the most comprehensive hands-on training
- Unlock high-paying career opportunities as a CEH v12 professional
- Get the ultimate CEH v12 course with top-notch resources for guaranteed success
- Get trained by EC Council-Certified trainers and ace the CEH v12 exam on the first go
Enterprise Training for Teams: Get a Quote
Professionals trained
Workshops every month
Countries and counting


Home
>
Cyber Security
>
EC-Council
>
Certified Ethical Hacking
Certified Ethical Hacking Course (CEH® v12)
Get ready to ace your CEH® v12 exam in the first go with the most comprehensive hands-on training
- Unlock high-paying career opportunities as a CEH v12 professional
- Get the ultimate CEH v12 course with top-notch resources for guaranteed success
- Get trained by EC Council-Certified trainers and ace the CEH v12 exam on the first go
Enterprise Training for Teams: Get a Quote
Professionals trained
Workshops every month
Countries and counting


Become a Skilled Ethical Hacker
If you’re looking to become a sought-after CEH v12 trained professional, our comprehensive training program is just what you need. Not only is our power-packed course designed to equip you with the knowledge and skills necessary to excel in the cybersecurity domain, it will also ensure that you clear your CEH v12 certification exam on the very first attempt.…..
Benefit from 40 hours of live instructor-led training, where our experienced instructors will guide you through interactive sessions, ensuring you have a solid foundation to tackle the CEH v12 exam with confidence. With expert-led on-demand courses by renowned ethical hacking experts, you’ll have access to 11+ hours of specialized training and 24+ hours of Python ethical hacking training, enabling you to deepen your understanding and gain hands-on experience from the best teachers in the industry.
Enhance your preparation with our extensive question bank, meticulously crafted with 500+ CEH v12 exam-focused questions. Practice makes perfect, and that’s why we provide you with two high-quality practice exams, consisting of 125 unique questions each. Each question comes with detailed explanations, allowing you to learn from both the correct and incorrect options, and refer back to the learning material for further study.
Take your learning to the next level with our hands-on experience component. Gain access to a 6-month membership to iLabs Cyber Range, where you can apply your knowledge in a real-world environment. This platform replicates industry challenges, allowing you to enhance your practical skills and readiness to tackle cybersecurity issues effectively.
In addition to the top-notch training, you’ll receive the official courseware from EC Council, ensuring you have the most up-to-date and relevant study materials. We also cover the exam fee, removing any financial burden and enabling you to focus solely on your preparation. Our step-by-step exam pass guide, curated by our UpSkill Finder experts, will provide you with exclusive insights and strategies to navigate the CEH v12 exam successfully on your first attempt.
Expand your expertise further with eight complimentary courses, collectively valued at US$ 6000. These self-paced courses delve deeper into related areas, strengthening your overall skill set and making you a well-rounded cybersecurity professional. Additionally, our comprehensive job assistance program offers resume and LinkedIn profile reviews, access to our extensive network of over 5,000 hiring partners, and a curated list of top interview questions and answers from our successful alumni.
UpSkill Finder is an Authorized Training Partner (ATP) and Accredited Training Center (ATC) of the International Council of E-Commerce Consultants, also known as EC-Council, the world’s largest cyber security technical certification body.
- 40 Hours of Live, Instructor-Led Sessions
- 6-Month Membership to iLabs Cyber Range
- 24+ Hours of On-Demand Python Ethical Hacking Course
- 2 High-Quality Practice Exams of 125 Questions Each
- 8 High-Quality Complimentary Courses Worth $6000
- Complete Career Support with Job Boost 360
- Training by Ethical Hacking Industry Experts
- 11+ Hours of On-Demand Ethical Hacking Course
- 500+ CEH v12 Exam-Focused Practice Questions
- Expert-Curated CEH v12 Exam Guide
- EC-Council Courseware, Exam Kit and Voucher
Benefits
This certified ethical hacking certification verifies the skills required to thrive in the information security domain. Many IT departments have made CEH compulsory for security-related posts. CEH-certified ethical hacker professionals earn 44 percent higher salaries than non-certified professionals.
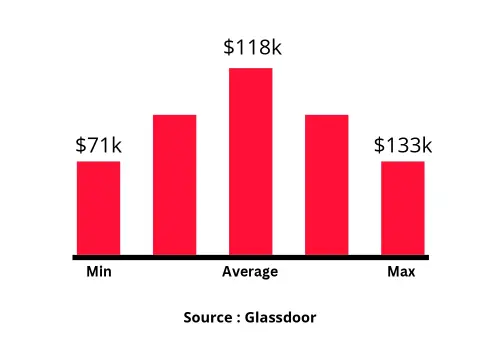
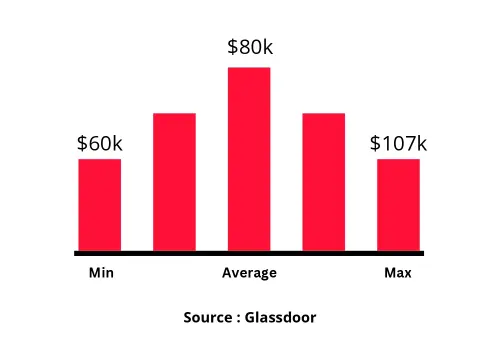
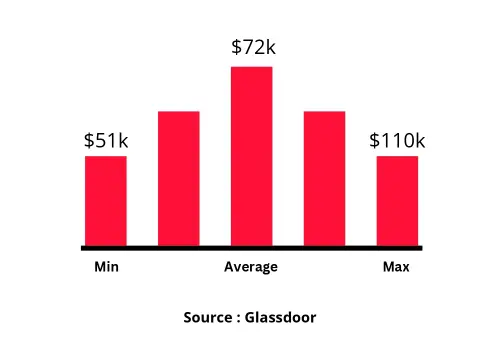
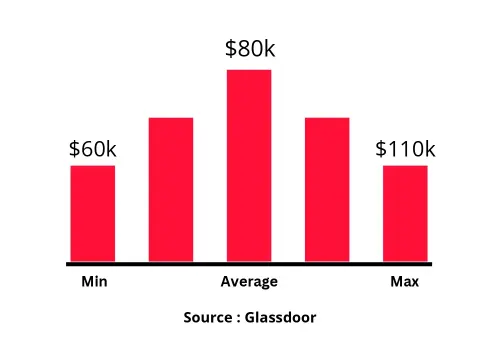
Designation
Annual Salary
Hiring Companies
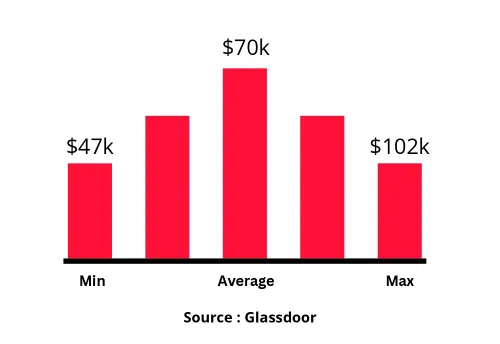
Tuition Fee and Training Options
- 40 Contact Hrs with Live, Instructor-led Session
- Mentor-Led Guaranteed Exam Pass Study Plan
- Unlimited Attempts to Mock Tests
- Premium Question Bank
- 40 Contact Hrs with Live, Instructor-led Session
- Mentor-Led Guaranteed Exam Pass Study Plan
- Unlimited Attempts to Mock Tests
- Premium Question Bank
Passing your CEH® V12 exam is key to getting your Certified Ethical Hacker certification and accelerating your cyber security career. What you need to crack the CEH exam in the very first go is a tried and tested learning path, curated by experts and designed to walk you through the exact steps you need to take to ensure success.
Just follow the steps below and be well on your way to acing your CEH exam and distinguish yourself as an expert Ethical Hacker:
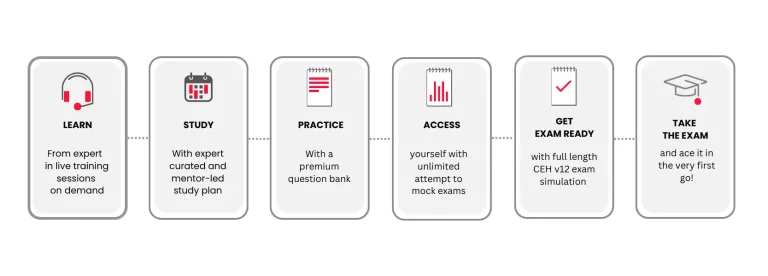
Prerequisites for Ethical Hacking Certification
- Two years of experience in Information Security is preferable, but not mandatory
- A foundational understanding of the information security industry and concepts of ethical hacking is beneficial for beginners
Why UpSkill Finder?
Comprehensive Learning Experience
Achieve CEH v12 exam mastery with our comprehensive live instructor-led training, ensuring interactive learning and guaranteed exam success.
Extensive Resources
Benefit from a question bank of 500+ CEH v12 exam-focused questions and practice with two high-quality exams, each comprising 125 questions.
Official EC Council Courseware
Access the official courseware from EC Council with the most up-to-date study materials for a solid foundation and success in the CEH v12 exam.
Support and Guidance
Get comprehensive support, including coverage of exam fee and a step-by-step exam pass guide curated by UpSkill Finder experts for exam success.
Complimentary Skill Development
Expand your expertise with 8 high-quality complimentary courses, collectively valued at US$ 6000, to enhance your overall skill set as a cybersecurity expert.
Career Assistance and Networking
Benefit from our Job Boost 360 career assistance program, including resume and LinkedIn profile reviews, connections to 5000+ hiring partners and more.
- Cover the fundamentals of key issues in the information security world, including the basics of ethical hacking, information security controls, relevant laws, and standard procedures.
- Learn how to use the latest techniques and tools to perform footprinting and reconnaissance, a critical pre-attack phase of the ethical hacking process.
- Learn different network scanning techniques and countermeasures.
- Learn various enumeration techniques, such as Border Gateway Protocol (BGP) and Network File Sharing (NFS) exploits, and associated countermeasures.
- Learn how to identify security loopholes in a target organization’s network, communication infrastructure, and end systems. Different types of vulnerability assessment and vulnerability assessment tools.
- Learn about the various system hacking methodologies—including steganography, steganalysis attacks, and covering tracks—used to discover system and network vulnerabilities.
- Learn different types of malware (Trojan, virus, worms, etc.), APT and fileless malware, malware analysis procedure, and malware countermeasures.
- Learn about packet-sniffing techniques and how to use them to discover network vulnerabilities, as well as countermeasures to defend against sniffing attacks.
- Learn social engineering concepts and techniques, including how to identify theft attempts, audit human-level vulnerabilities, and suggest social engineering countermeasures.
- Learn about different Denial of Service (DoS) and Distributed DoS (DDoS) attack techniques, as well as the tools used to audit a target and devise DoS and DDoS countermeasures and protections.
- Understand the various session hijacking techniques used to discover network-level session management, authentication, authorization, and cryptography weaknesses and associated countermeasures
- Get introduced to firewall, intrusion detection system (IDS), and honeypot evasion techniques; the tools used to audit a network perimeter for weaknesses; and countermeasures
- Learn about web server attacks, including a comprehensive attack methodology used to audit vulnerabilities in web server infrastructures and countermeasures.
- Learn about web application attacks, including a comprehensive web application hacking methodology used to audit vulnerabilities in web applications and countermeasures.
- Learn about SQL injection attacks, evasion techniques, and SQL injection countermeasures.
- Understand different types of wireless technologies, including encryption, threats, hacking methodologies, hacking tools, Wi-Fi security tools, and countermeasures
- Learn Mobile platform attack vector, android and iOS hacking, mobile device management, mobile security guidelines, and security tools.
- Learn different types of IoT and OT attacks, hacking methodology, hacking tools, and countermeasures.
- Learn different cloud computing concepts, such as container technologies and server less computing, various cloud computing threats, attacks, hacking methodology, and cloud security techniques and tools.
- Learn about encryption algorithms, cryptography tools, Public Key Infrastructure (PKI), email encryption, disk encryption, cryptography attacks, and cryptanalysis tools.
Ethical Hacking Certification FAQs
Our comprehensive CEH course is all about preparing you for the CEH v12 certification exam and equipping you with hands-on skills to excel in the cybersecurity domain. With live instructor-led training, expert-led on-demand courses, and hands-on experience in a real-world environment, you’ll gain a solid foundation and practical skills to tackle cybersecurity challenges effectively.
You’ll receive extensive exam preparation resources, including a question bank, practice exams, and the official courseware from EC Council. Additionally, you’ll benefit from complimentary self-paced courses to expand your expertise and a job assistance program for career support.
The CEH Course is a 40-hour long structured professional program for aspiring cyber professionals. You will also benefit from access to 11+ hours of specialized training and 24+ hours of Python ethical hacking training, to learn on your own schedule.
Ethical hacking is not very difficult to learn but the skills cannot be mastered overnight. You must patiently put in sufficient time and be dedicated to acquiring the necessary knowledge and skills. In addition, you must hone your creativity and problem-solving attitude. If your basic concepts and fundamentals are strong, you can build on them faster.
If you are passionate and enthusiastic to learn ethical hacking from scratch, go ahead and connect with professionals. This is a great way to get insights.
To lay the groundwork for your future actions, you can brush up your concepts and basic skills for which you can consider gaining command over the following:
- Programming
- Operating system
- Networking
- Cryptography
- Website hacking
Candidates for the (CEH) Certified ethical hacking certification course need to have a minimum of two years of experience in the information security field. For novices, it is ideal to have a foundational understanding of the information security industry and the concepts of ethical hacking.
Yes, our Certified Ethical Hacker course is accredited by EC-Council. It is considered the best course for ethical hacking. After you complete the ethical hacking course qualification, you can elevate your career with promising opportunities across diverse fields.
EC-Council believes in giving back to the security community as it has partaken of it. When you are a Certified Ethical Hacker, you are more than a security auditor or a vulnerability tester or a penetration tester alone. With the CEH v12 certification you are exposed to security checklists that will help you audit the organization’s information assets, tools which will check for vulnerabilities that can be exploited and above all a methodology to assess the security posture of your organization by doing a penetration test against it. In short, the knowledge you will acquire has practical value to make your workplace a more secure and efficient one.
Apart from the online resources available, you can refer to some books to gain knowledge and expertise to pass the CEH exam. These books will help you to understand your role in a better way.
Following is the list of the books that you can refer to:
- CEH Certified Ethical Hacker All-In-One Exam Guide, 4th edition by Matt Walker
- CEH Certified Ethical Hacker Bundle, 4th edition
- CEH v12 Certified Ethical Hacker Study Guide
- CEH Certified Ethical Hacker Practice Exams, 4th edition
- CEH v12: Certified Ethical Hacker Version 12 Kit, 1st edition
- Passing the CEH v12: Learning the Certified Ethical Hacker 12
- CEH v12: EC-Council Certified Ethical Hacker Complete Training Guide with Practice Labs
- Certified Ethical Hacker (CEH) Version 12 Cert Guide
The Certified Ethical Hacker Program is a comprehensive Training Program to train you on the most advanced and latest tools and techniques used by the grey hat or black hat hackers to break into the organization. This ethical hacking training online program provides an interactive, hands-on learning environment. According to CEH, there are five phases of ethical hacking that you will be dealing with:
- Reconnaissance
- Gaining access
- Enumeration
- Maintaining access
- Covering your tracks
There are four modes of learning through this CEH v12 training program which are as follows:
- iLearn (Self-study)
- iWeek (Live online)
- Master class (Live online)
- Training partner (In-person)
A candidate opting for CEH (Certified Ethical Hacker) training and certification course must have:
- A background in security-related experience
- Sound knowledge of TCP/IP
- Relevant work experience that reflects specialization in information security
Congratulations on becoming a CEH! It is considered the best ethical hacking course and also the best ethical hacking certification by many experts. Your next level is to become an EC-Council Certified Security Analyst (E|CSA) or proceed with the CEH (Practical).
Skills Covered
Scanning Networks
System Hacking
Cryptography
Sniffing
Malware Threats
Hacking Web Servers
DNS Cache Snooping
Vulnerability Analysis
Social Engineering
Denial-of-service
Session Hijacking
Evading IDS
Footprinting and Reconnaissance
Hacking Wireless Networks
Firewalls and Honeypots
Hacking Mobile Platforms
Secure Your Business with Ethical Hacking
Whether you seek to secure the data of your business or customer, all such objectives depend on a robust information security system and qualified professionals capable of handling modern day challenges. Skill up your information security professionals with the most in-demand ethical hacking credential.
- Custom Training Solutions
- Immersive Learning
- Learn by doing approach
- Immediately applicable skills
Skills You'll Gain with the CEH® v12 Training Online
Practical Experience
24 challenges across 4 levels of complexity, covering 18 attack vectors including OWASP Top 10
Greater Focus on Job-Readiness
Courseware and hands-on exercises based on a comprehensive industry-wide job-task analysis.
Security Standards
Master the five-phases of ethical hacking defined by the EC-Council updated for V12 framework.
Tool Repository
Learn the latest techniques and 3,500+ hacking tools for vulnerability assessment and security.
Hacking Web Applications
Learn the latest methods to hack Web API, Webhooks and Web shell concepts, and operating systems.
Focused Learning
Understand attacks targeted at mobile platforms for building countermeasures to secure mobile frameworks.
Real-Time Simulation
Work in iLabs cloud cyber range that simulates real-life networks and operating platforms.
Recommended Courses
Our Customers Feedback
- Email: [email protected]
- (+91) 92581 19067
- +966 53 004 6026
- +971 50 366 1756
- +974 3372 4821